The demand for safe and credible identification and authentication has rapidly increased, but the emphasis on the security of biometric images and feature templates is far from enough. Biometrics, including iris features, have a life-time constant character, which indicates that once lost, it means that it is permanently lost. There is no way to re-edit or publish templates to make up for the loss. The existence of these security threats is seriously restricting the further development of biometrics-based technology.
In the current application process of iris, the hidden dangers of the iris are mainly the leakage of the original iris image and the image restoration of the iris feature template. The specific description is as follows:
(1) The leakage of the original iris image: In the process of iris application in the public security field, the iris original image is a concentrated expression of personal privacy data, and there is a risk of privacy leakage. When a large area of ​​leakage occurs, it will have serious social impact.
(2) Image restoration of iris feature template : The iris feature template is restored to an iris image for other applications by some algorithms. Although the restored image is not identical to the original image, it can also be used for iris recognition or other iris algorithms. .
For the security risks of the above iris applications, we must study the cryptography-based original image and feature template protection scheme to protect the iris data to meet the security requirements of the user in the process of identity acquisition, storage and authentication. The lifetime immutability of iris features and the massive data in the system's iris image feature database all pose great challenges to the study of this technology, especially in the harsh requirements of authentication technologies such as the correct matching rate, false rejection rate, and authentication speed and other security objectives. Next, it is a severe test of whether this technology can achieve further development.
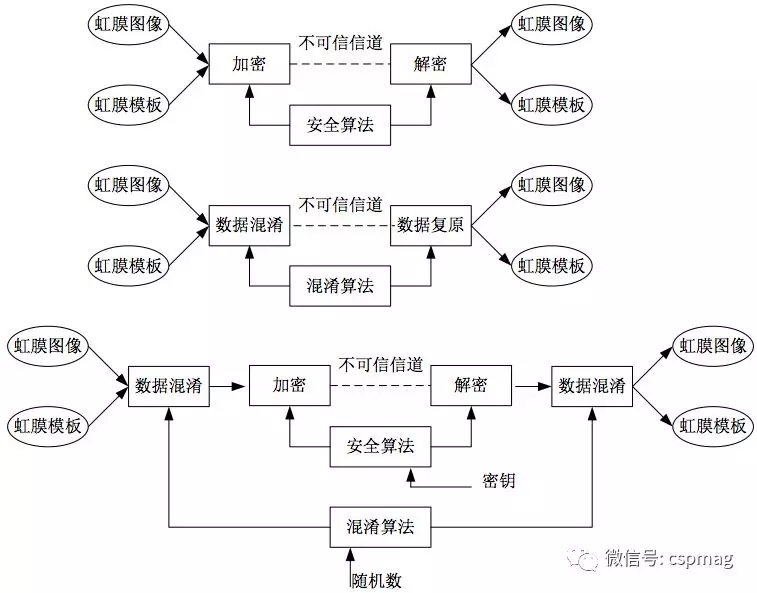
For biometric security, research institutions at home and abroad are mainly divided into two major technology schools: data encryption and data obfuscation. The method based on data encryption is to bind key and image/feature information, generate ciphertext for transmission, and play private data. The purpose of the protection, but relates to the issue of symmetric key distribution. Data obfuscation is mainly based on template deformation technology, random number conversation multi-factor obfuscation technology, digital watermarking, and biometric data mosaic. See Figure 1 for basic methods of iris data protection. Both methods cause some loss in the efficiency of iris collection, transmission, and comparison.
Figure 1 Iris data or template data encryption and data confusion
Professional big size CNC EDM Sinker machine manufacturer, the worktable fixed type. We supply best quality CNC EDM Sinker Machine quality and best price and best after service

Worktable Fixed CNC EDM Sinker
Worktable Fixed CNC EDM Sinker,CNC EDM Sinking Machine,CNC EDM Sinker,big size CNC EDM Sinker
Suzhou Simos CNC Technology Co., Ltd. , http://www.edm-machines.com